Article explaining how to convert java keystore jks into PEM formatted certificate or key file for Apache configuration
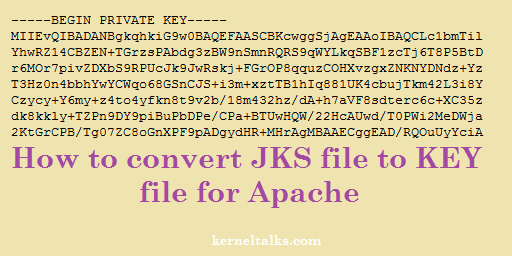
Scenario: I have a key file (*.jks) and CSR file generated in using keytool command i.e. in java. I wanted to convert this jks file to *.key file so that it can be used in Apache webserver configuration.
Read how to create java Keystore file *.jks if you want to know how to create CSR using java keytool.
Solution :
JKS file is Keystore used in java. You need to follow the below steps to get your unencrypted key file. Its a two-step process :
- Import key data from keystore to PKC12 format
- Convert PKCS12 key to un-encrypted PEM
Import key data from keystore to PKC12 format
We will import key data from jks Keystore to new Keystore in PKC12 format using keytool command where –
-srckeystore: Your jks file-destkeystore: Name of new keystore to create-deststoretype: Obv has to be PKCS12
You need to provide a password of the source Keystore and also set a new password to the new Keystore.
[root@kerneltalks ~]# keytool -importkeystore -srckeystore kerneltalks.com.jks -destkeystore keystore.pkcs12 -deststoretype PKCS12
Importing keystore kerneltalks.com.jks to keystore.p12...
Enter destination keystore password:
Re-enter new password:
Enter source keystore password:
Entry for alias server successfully imported.
Import command completed: 1 entries successfully imported, 0 entries failed or cancelled
Convert PKCS12 key to un-encrypted PEM
We now need to convert this PKCS12 key in PEM format so that it can be used in the Apache configuration.
[root@kerneltalks ~]# openssl pkcs12 -in keystore.pkcs12 -nodes -nocerts -out kerneltalks.com.key
Enter Import Password:
MAC verified OK
Now verify your private key file.
[root@kerneltalks ~]# file kerneltalks.com.key
kerneltalks.com.key: ASCII text
[root@kerneltalks ~]# file kerneltalks.com.jks
kerneltalks.com.jks: Java KeyStore
[root@kerneltalks ~]# cat kerneltalks.com.key
Bag Attributes
friendlyName: server
localKeyID: 54 69 6D 65 20 31 35 35 36 32 30 38 36 31 33 32 36 34
Key Attributes: <No Attributes>
-----BEGIN PRIVATE KEY-----
MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQCLc1bmTilYhwRZ
14CBZEN+TGrzsPAbdg3zBW9nSmnRQRS9qWYLkqSBF1zcTj6T8P5BtDr6MOr7pivZ
DXbS9RPUcJk9JwRskj+FGrOP8qquzCOHXvzgxZNKNYDNdz+YzT3Hz0n4bbhYwYCW
qo+768GSnCJS+i3m+xztTB1hIq881UK4cbujTkm42L3i8YCzycy+Y6my+z4to4yf
kn8t9v2b/18m432+hz/dA+h7aVF8sdterc6c+XC35zdk8kkly+TZPn9DY9piBuPb
DPe/CPa+BTUwHQW/22HcAUwd/T0PWi2MeDWja2KtGrCPB/Tg07ZC8oGnXPF9pADg
ydHR+MHrAgMBAAECggEAD/RQOuUyYciAvO6k6yjXd/myOtNBhULKccVra3veA2zY
vKJG5IgQfhx4KVRiYHawAEBohvtVxxjJ53lc4OHdNO70+UQfg3RwBAB8DroKwRjl
77T0ZZr1MQZSCC/efNLugI+8vMmAz9bDqXk2HJ/qc6WdX7Tzz3tnYdbVfamENwdb
7+w3isHa+XhsJdR9IrpPL35mf2HSeW2WgOMku/GWIdEcCGdxm0cZTx7X1JNBrimm
zAp1+5xVx3ptgrtRYYAihFjQLNvhp5twyAdK2mB4iOpU35c3KPWD2HqNfp0MYPNq
eRlqEdIxFimXMnRw4zSA7GuaSADv5ddS60529KK2IQKBgQC/fK99E/8iSk3UtZvz
/5PUSabnAUK73Z0N5QLZfGwSWF51q0zmxfVQInHXIGIFeqkjt8EOEiOIXi7XyA+c
FG8KBKIkXoeJ/Rzxskzp1yG0L2EePJbUSnxtL4PTqlVCW6H5/C6V4icaMx4nC1Od
4vWmAqtRKBCdF5fMEOKWcn6t8wKBgQC6bqAwQUe4WvcnySN2vjMJiLDPm4RpnnuJ
o1s3pkPDeXaDI+2nD8NJT6GaskJsQhuq9ikdecDljqJIoSi7hCqHO75pUDPWdHIG
QMiyR2OB4NOOCvFf9FuVEz7JMWa7vk+KVgtgaaX3wG7vqsaYJcQ/VgsBqtKDSKS6
j4gaJiECKQKBgEjxcVQfOvBQB8gAinDvKdwTVm3nEAnKiNpTI7u/ZteyLAF9CKVc
QW+OP3loj45wxF+jzvnSNRDsd8GhJzkYm5fgXfemvtD0x4LWne/yEJe3+LHw+K/T
1AQvtnL6DtJhX5l/1CsqZCTZ1iGfcfHSFCtyFtqqfXGqHBwTTo1q/hC7AoGBALbW
2/+3ZjFl9VNtrnw8WS2Wg2F4skorhhkcvs87HuZM72/6Ao9/pBT4JhPjk8U8qIno
1bX0vLvmQT5d3+bX3iW28C203MIMfe+oBazi2rJ73r9F+CgVLORtdXw4GPsz0Cpp
7MpnksACWEpxAEgjce5z4mOGNuNOkU/uiJqsnl7RAoGAb5JbI7nBMJbUQp6QaZjN
tn1ZIaYEF+wyx2XR12iaqWG8RGwLcayZ55wjlAgO+qx3aYoheU4BTlqQiZMP+ytp
vUfV2rbexdqkvQAefg4kFkrFtOMQ7gzVWoIbWIhd5xyEtonvX3lqkm+c/kpxcruP
xe2Elr6dfovdXXadgIBDiSA=
-----END PRIVATE KEY-----
To use this key file in Apache configuration you need to strip off a header. Delete all parts till -----BEGIN PRIVATE KEY----- and save the file. Now you are good to use this *.key file in Apache SSL configuration.
How to export certificate from JKS file
As an addon to this post, I will walk you through how to export a certificate from java Keystore to PEM format. This is again two-step exercise as below –
Export certificate in binary
You read from the Keystore file certificate associated with alias and export it to a binary file. I used alias as server while creating this jks file hence options are –
-export: To export data. This is same asexportcertin newer versions-alias: Enter same alias you used while creating this java key file-file: Destination binary file in which you will export-keystore: Your jks key file
[root@kerneltalks ~]# keytool -export -alias server -file kerneltalks.com.der -keystore kerneltalks.com.jks
Enter keystore password:
Certificate stored in file <kerneltalks.com.der>
Warning:
The JKS keystore uses a proprietary format. It is recommended to migrate to PKCS12 which is an industry standard format using "keytool -importkeystore -srckeystore kerneltalks.com.jks -destkeystore kerneltalks.com.jks -deststoretype pkcs12".
Convert exported certificate data to PEM format
Now we will convert certificate binary to PEM format using below command where –
-in: Input binary means exported file in last command-out: Output file in PEM format
Now verify your certificate file.
[root@kerneltalks ~]# openssl x509 -inform der -in kerneltalks.com.der -out certificate.pem
[root@kerneltalks ~]# file certificate.pem
certificate.pem: PEM certificate
[root@kerneltalks ~]# cat certificate.pem
-----BEGIN CERTIFICATE-----
MIIDhzCCAm+gAwIBAgIEXVVftjANBgkqhkiG9w0BAQsFADB0MQswCQYDVQQGEwJJ
TjEUMBIGA1UECBMLTWFoYXJhc2h0cmExDzANBgNVBAcTBk11bWJhaTERMA8GA1UE
ChMIUGVyc29uYWwxETAPBgNVBAsTCFBlcnNvbmFsMRgwFgYDVQQDEw9rZXJuZWx0
YWxrcy5jb20wHhcNMTkwNDI1MTYwNzQ3WhcNMTkwNzI0MTYwNzQ3WjB0MQswCQYD
VQQGEwJJTjEUMBIGA1UECBMLTWFoYXJhc2h0cmExDzANBgNVBAcTBk11bWJhaTER
MA8GA1UEChMIUGVyc29uYWwxETAPBgNVBAsTCFBlcnNvbmFsMRgwFgYDVQQDEw9r
ZXJuZWx0YWxrcy5jb20wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCL
c1bmTilYhwRZ14CBZEN+TGrzsPAbdg3zBW9nSmnRQRS9qWYLkqSBF1zcTj6T8P5B
tDr6MOr7pivZDXbS9RPUcJk9JwRskj+FGrOP8qquzCOHXvzgxZNKNYDNdz+YzT3H
z0n4bbhYwYCWqo+768GSnCJS+i3m+xztTB1hIq881UK4cbujTkm42L3i8YCzycy+
Y6my+z4to4yfkn8t9v2b/18m432+hz/dA+h7aVF8sdterc6c+XC35zdk8kkly+TZ
Pn9DY9piBuPbDPe/CPa+BTUwHQW/22HcAUwd/T0PWi2MeDWja2KtGrCPB/Tg07ZC
8oGnXPF9pADgydHR+MHrAgMBAAGjITAfMB0GA1UdDgQWBBTpp/RefN3Sym3rmhFo
oztuqM3H8DANBgkqhkiG9w0BAQsFAAOCAQEAYJ5r7dR/HMpiZis/JQK91njTayYY
v/ucXcc5uFQN6UyteGNmQuC8/7XtURks3gtwJXcrrtOgW9Vc4OSaR05Fwa+IHX53
123SygEfV/3hkTAznHp1xYXtRInOVU8O3U77s9MPbdGEK1mJRn8o0e82OORVd1Zx
u6BJW6K3sNt4odIeWcFJRzh8RA8pN+/zniiVxiM9wzI3pz2u5t8Rb9X/6oWBG75e
BFGzF56rQj2jx0o9aZP55uKHjY0YsTrck52nJi8bRKNfBhM6ojMhWOPu58/Wl0sM
rr6G9sBbkk/jBDf4qXxhDqnuPMXjCyLp7dhScrp5F3Qt61xWWDVnkgmbng==
-----END CERTIFICATE-----