Step by step guide to configure telnet server on Linux. Generally, SSH is preferred over telnet since its more secure, and hence telnet is not available out of the box.
Telnet (TELetype NETwork) is a network protocol used on the Internet or local area networks. It uses a virtual terminal connection and provides bidirectional interactive text-oriented communication. One can use telnet to log in remotely to another system locally or over the internet.
Caution: telnet open un-encrypted communication channel to your machine over the network. Avoid using telnet and opt SSH for connectivity.
SSH i.e. Secure SHell is more secure than telnet. Hence, all Linux Unix servers use SSH for user connectivity. Even many installations don’t have telnet available out of the box.
This tutorial walks you through the process to configure telnet on your Linux machine but SSH is always advisable for server connectivity than telnet for being more secure.
telnet server configuration :
Step 1:
As I said above, many installations don’t have telnet out of the box. You need to install the telnet package as a first step. Install telnet, telnet-server, and xinetd packages.
Use apt-get install telnetd for debian, ubuntu distro.
# yum install telnet telnet-server xinetd
Loaded plugins: amazon-id, rhui-lb, security
Setting up Install Process
Resolving Dependencies
--> Running transaction check
---> Package telnet.x86_64 1:0.17-48.el6 will be installed
---> Package telnet-server.x86_64 1:0.17-48.el6 will be installed
---> Package xinetd.x86_64 2:2.3.14-40.el6 will be installed
--> Finished Dependency Resolution
Dependencies Resolved
=============================================================================================================================================================
Package Arch Version Repository Size
=============================================================================================================================================================
Installing:
telnet x86_64 1:0.17-48.el6 rhui-REGION-rhel-server-releases 58 k
telnet-server x86_64 1:0.17-48.el6 rhui-REGION-rhel-server-releases 37 k
xinetd x86_64 2:2.3.14-40.el6 rhui-REGION-rhel-server-releases 122 k
Transaction Summary
=============================================================================================================================================================
Install 3 Package(s)
Total download size: 217 k
Installed size: 423 k
Is this ok [y/N]: y
Downloading Packages:
(1/3): telnet-0.17-48.el6.x86_64.rpm | 58 kB 00:00
(2/3): telnet-server-0.17-48.el6.x86_64.rpm | 37 kB 00:00
(3/3): xinetd-2.3.14-40.el6.x86_64.rpm | 122 kB 00:00
-------------------------------------------------------------------------------------------------------------------------------------------------------------
Total 335 kB/s | 217 kB 00:00
Running rpm_check_debug
Running Transaction Test
Transaction Test Succeeded
Running Transaction
Installing : 2:xinetd-2.3.14-40.el6.x86_64 1/3
Installing : 1:telnet-server-0.17-48.el6.x86_64 2/3
Installing : 1:telnet-0.17-48.el6.x86_64 3/3
Verifying : 1:telnet-server-0.17-48.el6.x86_64 1/3
Verifying : 1:telnet-0.17-48.el6.x86_64 2/3
Verifying : 2:xinetd-2.3.14-40.el6.x86_64 3/3
Installed:
telnet.x86_64 1:0.17-48.el6 telnet-server.x86_64 1:0.17-48.el6 xinetd.x86_64 2:2.3.14-40.el6
Complete!
Step 2:
Set services to start on boot.
# chkconfig telnet on
# chkconfig xinetd on
Restart services. inetd in case of Debian.
# service xinetd restart
Stopping xinetd: [FAILED]
Starting xinetd: [ OK ]
Verify service is listening on your server.
# netstat -lptu|grep telnet
tcp 0 0 *:telnet *:* LISTEN 1618/xinetd
# lsof -i |grep telnet
xinetd 1618 root 5u IPv6 13908 0t0 TCP *:telnet (LISTEN)
Step 3:
Connect your server from a windows machine with the telnet protocol. Open a command prompt and type telnet IP-address. You will be greeted with a login prompt and will be able to login with an existing user.
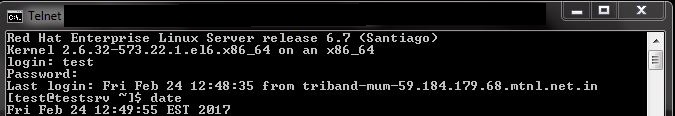
If you are not able to connect via telnet make sure there are no firewalls are blocking communication between your Windows machine and telnet server for port 23 TCP.