Step by step rundown to troubleshoot AWS cross-account assume role issues.

AWS cross-account role access is one of the most common use cases in cloud environments and is always a headache to troubleshoot if one is not familiar enough with IAM. In this article, we will walk you through step by step procedure to drill down into the root cause of why AWS cross-account IAM role access is not working.
Typically, you will be seeing error messages like –
An error occurred (AccessDeniedException) when calling the xxx operation: User: arn:x....x is not authorized to perform xxx:xxx on resource arn:x....x because no resource-based policy allows the xxx:xxx action.
Let’s formalise the legends for a better understanding of the below steps:
account1is the account from which role assume request is initiatedaccount2is the account in which targetrole2exists and IAM entity fromaccount1is trying to assume it.- IAM entity from
account1can be IAM user or role.
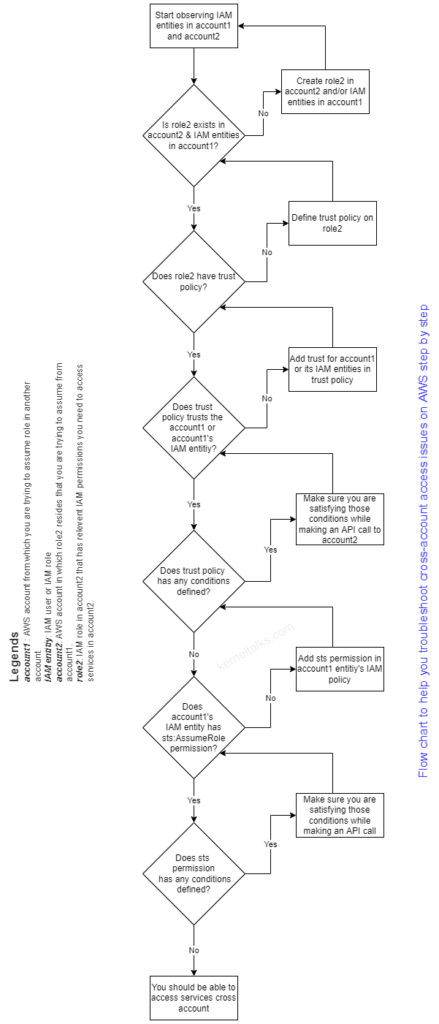
Consider below steps/points that will help you troubleshoot cross-account access issues.
account1IAM entity (user/role)should have permissionsts:AssumeRoledefined in IAM policy attached to it. If it has someconditionattached to it, those conditions must be satisfied in the assume call.account2‘s IAM rolerole2should have trust policy defined. This trust policy should trusts (principalfield) theaccount1oraccount1‘s IAM entity (user/role) which is initiating the assume call.- If trust policy is having
conditiondefined (conditionfield), then assume call should be satisfying those conditions. account2‘s IAM role must have permissions properly defined that account1’s IAM entity want to use inaccount2.
Or you can go through the below flow chart and drill down to the root cause of your problem!
Share Your Comments & Feedback: