Learn how to start, stop & restart the MariaDB server in Linux. Also, know how to check the MariaDB server status.
MariaDB is a MySQL database management system and popular nowadays.
It is one of the pillars of the LAMP stack popular among developers. In this article, we will walk you through steps to manage the MariaDB server process from the command line shell prompt.
In newer systems like RHEL 7, Debian 8, Ubuntu 15.04, Suse 12 and later system V init daemon is replaced by systemd. We will see both systemd and system V init commands to manage the MariaDB server process. Be noted that we are dealing with the MariaDB server process only. You have to take care of the databases you build within for their graceful shutdown and startup.
How to start MariaDB server
On newer systems with systemd
# systemctl start mariadb
On older systems with system V init
# service mysql start
Starting MariaDB.190110 07:15:32 mysqld_safe Logging to 'https://z5.kerneltalks.com/var/lib/mysql/kerneltalks.test.err'.
190110 07:15:32 mysqld_safe Starting mysqld daemon with databases from /var/lib/mysql
. [ OK ]
How to start MariaDB server at boot
On newer systems with systemd
# systemctl enable mariadb
ln -s 'https://z5.kerneltalks.com/usr/lib/systemd/system/mariadb.service' 'https://z5.kerneltalks.com/etc/systemd/system/multi-user.target.wants/mariadb.service'
On older systems with system V init
Systems like RHEL, CentOS, SUSE uses chkconfig to manage processes at boot.
# chkconfig --add mysql
# chkconfig --level 345 mysql on
Systems like Debian, ubuntu uses update-rc.d
# update-rc.d mysql defaults
How to stop MariaDB server
On newer systems with systemd
# systemctl stop mariadb
On older systems with system V init
# service mysql stop
Shutting down MariaDB. [ OK ]
How to check MariaDB server status
On newer systems with systemd
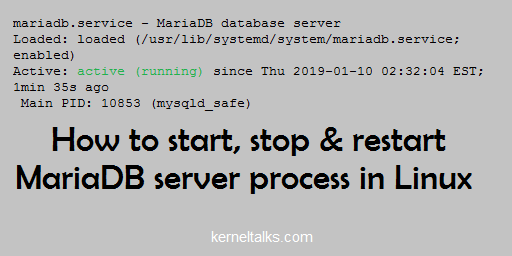
# systemctl status mariadb
mariadb.service - MariaDB database server
Loaded: loaded (/usr/lib/systemd/system/mariadb.service; enabled)
Active: active (running) since Thu 2019-01-10 02:32:04 EST; 1min 35s ago
Main PID: 10853 (mysqld_safe)
CGroup: /system.slice/mariadb.service
├─10853 /bin/sh /usr/bin/mysqld_safe --basedir=/usr
└─11015 /usr/libexec/mysqld --basedir=/usr --datadir=/var/lib/mysql --plugin-dir=/usr/lib64/mysql/plugin --log-error=/var/log/mariadb/mariadb.log --pid-fi...
Jan 10 02:32:00 ip-172-31-89-93.ec2.internal mariadb-prepare-db-dir[10775]: MySQL manual for more instructions.
Jan 10 02:32:00 ip-172-31-89-93.ec2.internal mariadb-prepare-db-dir[10775]: Please report any problems at http://mariadb.org/jira
Jan 10 02:32:00 ip-172-31-89-93.ec2.internal mariadb-prepare-db-dir[10775]: The latest information about MariaDB is available at http://mariadb.org/.
Jan 10 02:32:00 ip-172-31-89-93.ec2.internal mariadb-prepare-db-dir[10775]: You can find additional information about the MySQL part at:
Jan 10 02:32:00 ip-172-31-89-93.ec2.internal mariadb-prepare-db-dir[10775]: http://dev.mysql.com
Jan 10 02:32:00 ip-172-31-89-93.ec2.internal mariadb-prepare-db-dir[10775]: Consider joining MariaDB's strong and vibrant community:
Jan 10 02:32:00 ip-172-31-89-93.ec2.internal mariadb-prepare-db-dir[10775]: https://mariadb.org/get-involved/
Jan 10 02:32:01 ip-172-31-89-93.ec2.internal mysqld_safe[10853]: 190110 02:32:01 mysqld_safe Logging to 'https://z5.kerneltalks.com/var/log/mariadb/mariadb.log'.
Jan 10 02:32:01 ip-172-31-89-93.ec2.internal mysqld_safe[10853]: 190110 02:32:01 mysqld_safe Starting mysqld daemon with databases from /var/lib/mysql
Jan 10 02:32:04 ip-172-31-89-93.ec2.internal systemd[1]: Started MariaDB database server.
On older systems with system V init
# service mysql status
MariaDB running (2122) [ OK ]
How to restart MariaDB server process
On newer systems with systemd
root@kerneltalks # systemctl restart mariadb
On older systems with system V init
root@kerneltalks # service mysql restart
Shutting down MariaDB.... [ OK ]
Starting MariaDB.190110 07:35:01 mysqld_safe Logging to 'https://z5.kerneltalks.com/var/lib/mysql/ip-172-31-90-145.ec2.internal.err'.
190110 07:35:01 mysqld_safe Starting mysqld daemon with databases from /var/lib/mysql
. [ OK ]