GitHub action code for automated CloudFormation template linting on PR
GitHub is a popular version control software used widely by companies. And it is the best place to manage your AWS IaC i.e. CloudFormation templates! With the ever-growing AWS infrastructure and hence the template versions, it’s always a good practice to have your CloudFormation templates linted for any syntax errors. It saves a lot of time as you know the errors beforehand and not at the time of deployment on AWS! It will be more time saving if it just gets linted when someone raises the pull request (PR) so that the code owner, as well as the developer, knows the code modifications in PR are linted and sane to be approved.
cfn-linter is the best CloudFormation linter available. It can be implemented via GitHub actions for automated lint actions on PR submission. I will walk you through the process of setting it up.
Understanding the flow
First of all, you need to get the list of modified files in the PR so that you can run a linter against it. It can be managed by using readymade available actions or using git commands. There are a couple of actions like tj-actions, Get all changed files, etc.
Once we got the list, we need to filter out files that are potentially not CloudFormation templates. You don’t want to feed non-template files to linter as that would result in failure. I did this using grep and also allowed the shell to continue even if grep exists with a non-zero exit code. This will prevent GitHub action from failing if there are no template files modified in the given PR.
Lastly, lint all templates one by one using cfn-lint. I am ignoring the warning using -i W flag to avoid failing GitHub actions due to warnings.
Code
All these points are summarised in below GitHub Action code –
name: Lint CloudFormation Templates
on:
pull_request:
branches:
- main
jobs:
cloudformation-linter:
runs-on: ubuntu-latest
steps:
- name: Checkout
uses: actions/checkout@v2
- name: Setup Cloud Formation Linter with Latest Version
uses: scottbrenner/cfn-lint-action@v2
- name: Fetch changed file list
uses: tj-actions/changed-files@v17.2
id: changed-files
- name: Run Linter
shell: bash
run: |
> list
for file in ${{ steps.changed-files.outputs.all_changed_files }}; do
echo $file >> list
done
set +e
cat list | grep -e json -e yaml -e yml | grep -v .github > lint_list
set -e
if [ -s lint_list ]; then
for i in `cat lint_list`
do
echo "Linting template: $i"
cfn-lint -t $i -i W
done
else
echo "No Cloudformation template detected in commit!"
exit 0
fi
You need to place this file with the name of your choice under <repo>/.github/workflows the directory. If you have some different master branch naming conventions or different strategies on when code should be listed, then make necessary changes in on: section.
GitHub Action
Once the action config is in place, PR submission will see automated checked in it.
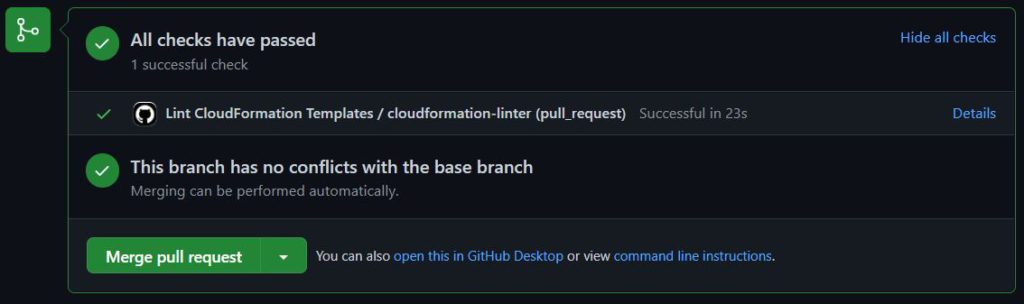
If you click on Details, you will see the details about the action.
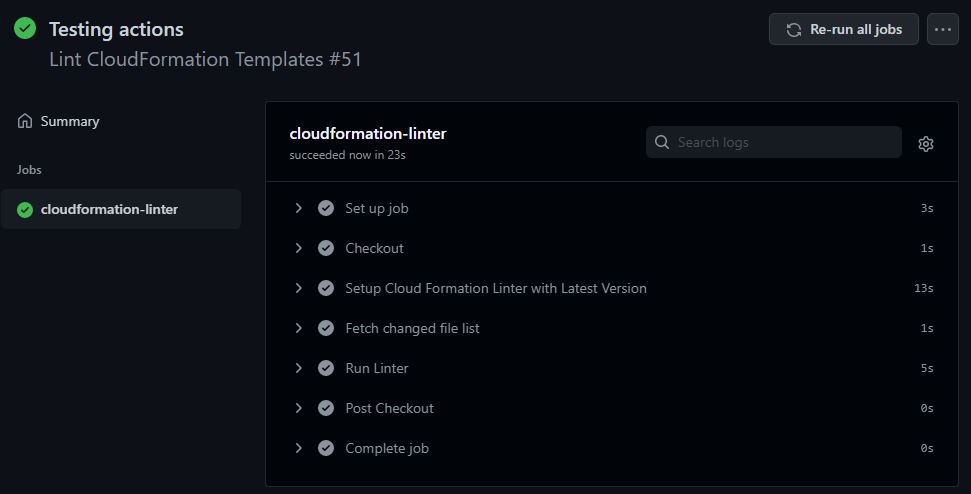
Your CloudFormation templates are being linted when PR is raised!
Share Your Comments & Feedback: