Quick post about how to remove the products channels in Suse Manager
There is a way you can add products and their channels in the Suse Manager server using the command line and webpage GUI. But once added it’s not easy to get them removed from the web console. Web console does not provide a direct option to remove product channels from Suse Manager. Also, the command used for adding channel i.e.. mgr-sync also does not support any option to remove channels.
So many of first time Suse Manager administrators stumble upon roadblock on how to remove product channels which are no more needed.
So let’s get started on the process to remove product channels (using command spacewalk-remove-channel) you might have added by mistake on Suse Manager or which are no longer needed and eating up your disk space.
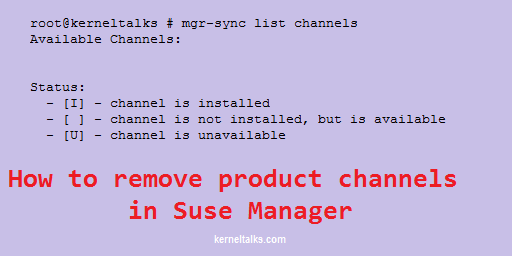
First, you need to list out all the channels on your Suse Manager using mgr-sync list command –
root@kerneltalks # mgr-sync list channels
Available Channels:
Status:
- [I] - channel is installed
- [ ] - channel is not installed, but is available
- [U] - channel is unavailable
[ ] RHEL6-Pool for x86_64 RHEL6 Base x86_64 [rhel6-pool-x86_64]
[I] SLE-Product-HPC-15-Pool for x86_64 SUSE Linux Enterprise High Performance Computing 15 x86_64 [sle-product-hpc-15-pool-x86_64]
[ ] SLE-Module-Basesystem15-Debuginfo-Pool for x86_64 Basesystem Module 15 x86_64 [sle-module-basesystem15-debuginfo-pool-x86_64-hpc]
[ ] SLE-Module-Basesystem15-Debuginfo-Updates for x86_64 Basesystem Module 15 x86_64 [sle-module-basesystem15-debuginfo-updates-x86_64-hpc]
[I] SLE-Module-Basesystem15-Pool for x86_64 Basesystem Module 15 x86_64 [sle-module-basesystem15-pool-x86_64-hpc]
[I] SLE-Module-Basesystem15-Updates for x86_64 Basesystem Module 15 x86_64 [sle-module-basesystem15-updates-x86_64-hpc]
...
Here let’s consider we need to remove channel sle-product-hpc-15-pool-x86_64. So first you need to remove all the child channels from this base product channel & then you will be able to remove the base channel. If you try to remove parent channel directly without removing child channels you will hit below error –
root@kerneltalks # spacewalk-remove-channel -c sle-product-hpc-15-pool-x86_64
Error: cannot remove channel sle-product-hpc-15-pool-x86_64: subchannel(s) exist:
sle-module-basesystem15-pool-x86_64-hpc
sle-module-basesystem15-updates-x86_64-hpc
sle-module-devtools15-pool-x86_64-hpc
....
You can clearly see child channels to be removed before you try for parent channel. This is also a good way to get a child channel list quickly!
Then go ahead, remove the child channel followed by base one. For example, see below child channel removal output –
root@kerneltalks # spacewalk-remove-channel -c sle-module-devtools15-pool-x86_64-hpc
Deleting package metadata (204):
________________________________________
Removing: ######################################## - complete
Repeat the process and remove all child channels one by one. You can use shell loops to get it done quicker. Finally, remove your parent channel, and you are done.
root@kerneltalks # spacewalk-remove-channel -c sle-product-hpc-15-pool-x86_64
Deleting package metadata (3):
________________________________________
Removing: ######################################## - complete
Once done you can confirm that channel is no more enabled in webpage console or using mgr-sync list command.